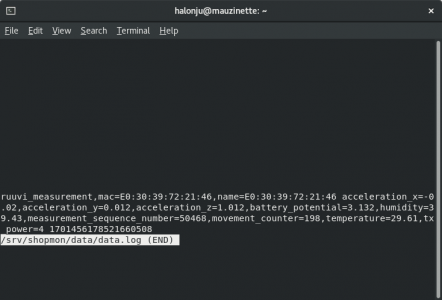
- Joined
- Aug 9, 2023
- Messages
- 439
Ubuntu Server 22.04 is considered fairly safe, but there is still a couple of good hardening practices we should implement just in case.
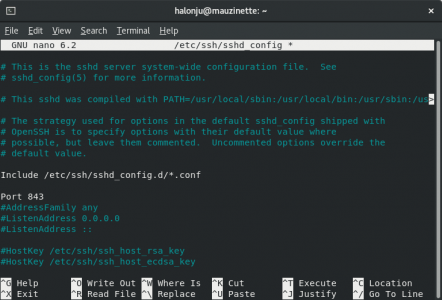
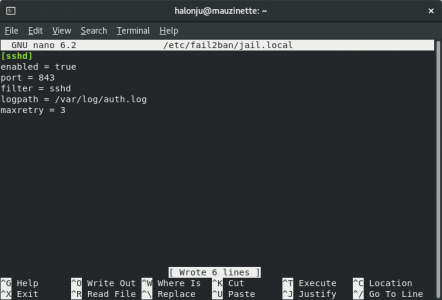
First we'll change the default SSH port to 843, as we don't want to assign it to an unprivileged port (≥1024). Let's make a backup of the configuration file and edit it using nano...
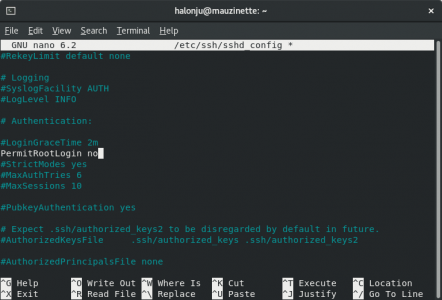
...and while we're at it, we should also disable root login and save the changes:
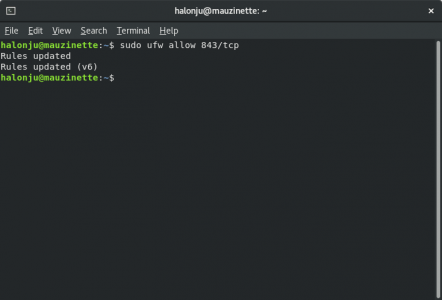
Next we'll configure the firewall to allow incoming connections to port 843:
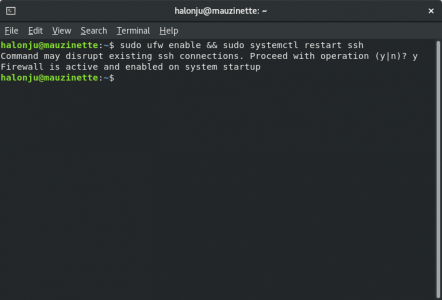
Then we'll enable the firewall and restart the ssh service.
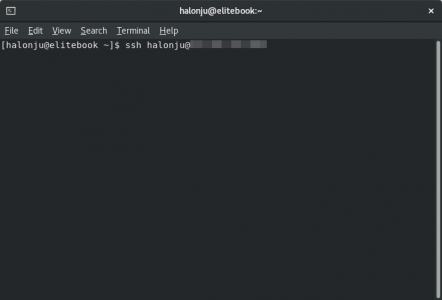
Now if we try to reconnect using the default SSH port, the connection gets refused:
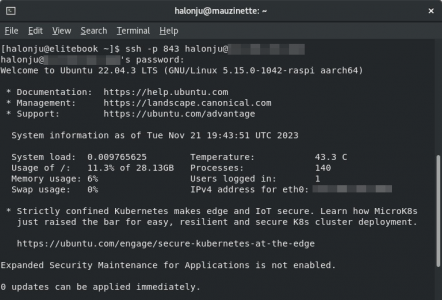
To successfully establish an SSH connection, we need to specify the port using the -p option flag:
First we'll change the default SSH port to 843, as we don't want to assign it to an unprivileged port (≥1024). Let's make a backup of the configuration file and edit it using nano...
Bash:
$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
$ sudo nano /etc/ssh/sshd_config
...and while we're at it, we should also disable root login and save the changes:

Next we'll configure the firewall to allow incoming connections to port 843:
Bash:
$ sudo ufw allow 843/tcp
Then we'll enable the firewall and restart the ssh service.
Bash:
$ sudo ufw enable && sudo systemctl restart ssh
Now if we try to reconnect using the default SSH port, the connection gets refused:

To successfully establish an SSH connection, we need to specify the port using the -p option flag:
Bash:
$ ssh -p 843 halonju@***.***.***.***
Last edited:



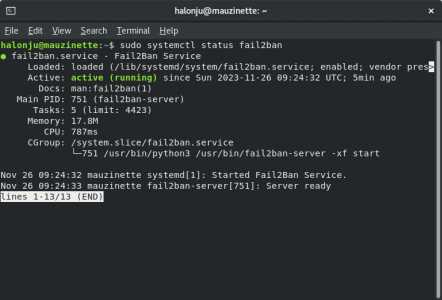
 To achieve this, we'll use the lightweight, 100% written in Rust
To achieve this, we'll use the lightweight, 100% written in Rust